The rapid changes in information technology today do not only affect IT security specialists. Developers, users and testers, but also managers at various levels of decision-making, especially in small and medium-sized companies and public authorities, require a wide range of qualifications and a deep understanding of the significance and consequences of IT security problems.
Cybersecurity is the top priority for achieving digital sovereignty. Therefore, a sufficient number of specialists with a high level of qualification in the field of cyber security is required for business and public authorities. Politics and business agree that the topic of cyber security is of central importance.
Our range of services
- Learning Lab Cybersecurity
The Cybersecurity Learning Lab (Production Consortium) is a cooperation between Fraunhofer IOSB, Fraunhofer IOSB-INA and Ostwestfalen-Lippe University of Applied Sciences at the Karlsruhe and Lemgo sites. Specialists and managers from industry and public administration receive compact training in high-quality laboratories with the latest IT infrastructure. There, they simulate real threat scenarios, learn to recognize their significance and consequences and study suitable solution concepts in terms of their practical application and effectiveness. Based on proven cooperation models between Fraunhofer and universities of applied sciences, a model is being implemented for the further training of IT security specialists that integrates the universities of applied sciences as partners in cooperative research, in the development of further training concepts and teaching modules and finally in the teaching of the course content.
- Secure Industry 4.0 Communication
Industry 4.0 applications such as condition monitoring, plug & work and optimization require secure communication. These security requirements can be realized through the use of OPC UA
- Industry 4.0 Applications
- Creation of information models
- Securing communication
- Protection according to IEC 62443
In the course of the digital transformation, companies must know their critical systems, assets and values in order to take appropriate protective measures. With IEC 62443, companies can protect themselves with a holistic security concept that supports the requirements of component manufacturers, machine builders and plant operators.
- Overview IEC 62443
- Design and implementation of a Cyber Security Management System (CSMS)
- Risk assessment and analysis
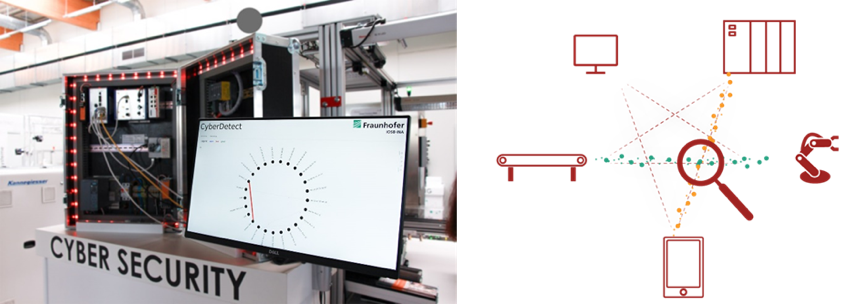
- Cyber Detect: real-time detection of cyber attacks for production systems
Cyber Detect is an analysis software for detecting network-based cyber attacks on industrial production systems. For this purpose, the communication between controllers and field devices is analyzed in real-time (see figure 1).
The analysis software checks the communication data for anomalies. If an anomaly occurs, an alarm is generated. The alarm allows manual and automatic countermeasures to be initiated, e.g. the production system can be put into a safe state. Cyber Detect has standardized interfaces like OPC UA to ensure easy integration and configuration.
Functions:
- Classification of cyber attacks
- Anomaly detection
- Real-time analysis
- Deep Packet Inspection
- Standardized interface through OPC UA

 Industrial Automation branch INA
Industrial Automation branch INA